[ad_1]
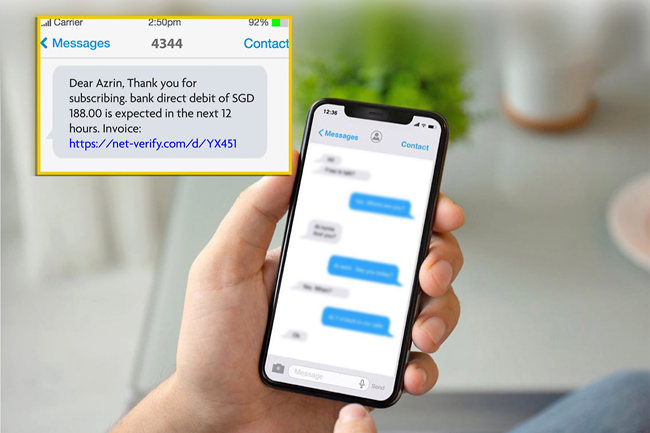
Financial institution Islam Brunei Darussalam (BIBD) suggested the general public to train warning in mild of the growing variety of ‘smishing’ incidents during which scammers might impersonate financial institution staff, a launch said yesterday.
‘Smishing’ is a type of phishing during which scammers ship out textual content messages which look like from somebody identified to the receiver.
These messages might comprise a shortened hyperlink that can redirect the receiver to a pretend web site with the purpose of acquiring confidential data.
In some circumstances, victims obtain an SMS or direct message from scammers who could also be posing as financial institution staff, during which victims had been requested to click on on a hyperlink to confirm sure transactions, or to validate their Web banking accounts.
These hyperlinks will redirect the victims to a pretend web site during which victims are instructed to supply their Web banking or credit score or debit card particulars together with a one-time password (OTP).
BIBD assured the general public that the financial institution won’t problem textual content hyperlinks with a clickable hyperlink for any promotions or campaigns by means of SMS, nor will financial institution personnel ask for data equivalent to private particulars, private login particulars, account particulars, card particulars, Web banking particulars or OTP’s over the telephone or by means of SMS.
BIBD additionally suggested the general public to watch the next measures stop falling sufferer to the scams:
– Keep away from clicking on sudden hyperlinks acquired by way of WhatsApp, SMS or social media.
– By no means disclose private particulars, financial institution login particulars, credit score/debit card particulars and OTP to anybody.
– At all times confirm the authenticity of any textual content messages or calls claiming to be from BIBD by contacting the BIBD Name Centre immediately at 2238181.
– Inform BIBD instantly if monetary particulars are suspected to have been compromised.
[ad_2]
Source link


