[ad_1]

Researchers following the actions of superior persistent (APT) menace teams originating from China, North Korea, Iran, and Turkey say that journalists and media organizations have remained a continuing goal for state-aligned actors.
The adversaries are both masquerading or attacking these targets as a result of they’ve distinctive entry to private data that might assist broaden a cyberespionage operation.
Current focusing on exercise
Proofpoint analysts have been following these actions from 2021 and into 2022 and revealed a report about a number of APT teams impersonating or focusing on journalists.
The China-linked menace actor referred to as ‘Zirconium’ (TA412) has been confirmed to focus on American journalists since early 2021 with emails containing trackers that alerted when messages have been accessed.
This straightforward trick additionally allowed the menace actor to acquire the goal’s public IP deal with from which they may collect extra data reminiscent of location of the sufferer and the web service supplier (ISP).
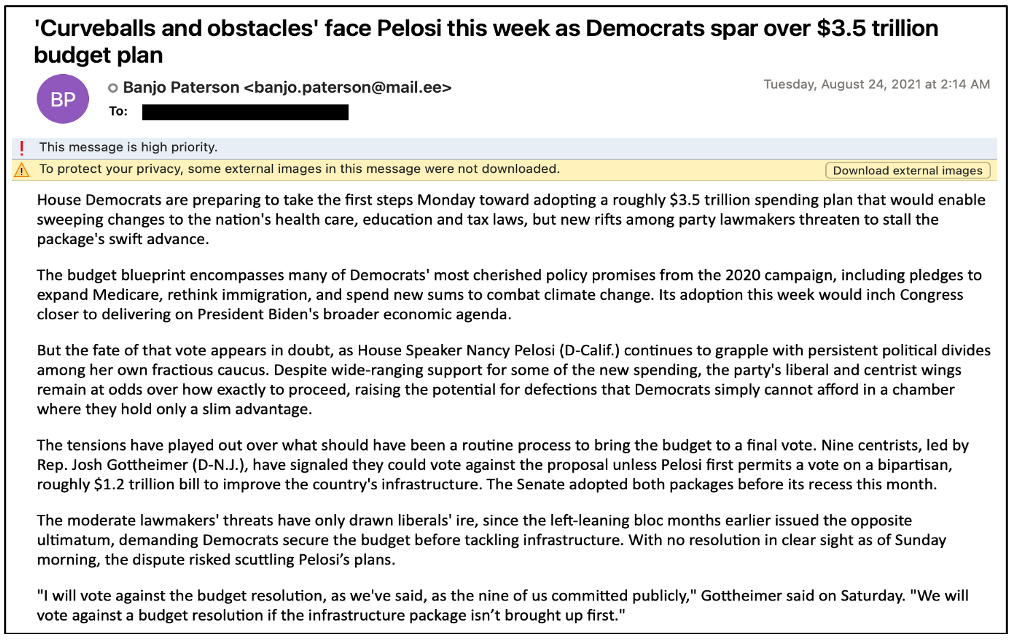
By February 2022, Zirconium resumed campaigns focusing on journalists with the identical techniques, focusing primarily on these reporting concerning the Russia-Ukraine struggle.
In April 2022, Proofpoint noticed one other Chinese language APT group tracked as TA459 focusing on reporters with RTF recordsdata that dropped a replica of the Chinoxy malware when opened. This group focused media inquisitive about international coverage in Afghanistan.
North Korean hackers of the TA404 group have been additionally noticed focusing on media personnel throughout the spring of 2022, utilizing pretend job postings as lures.
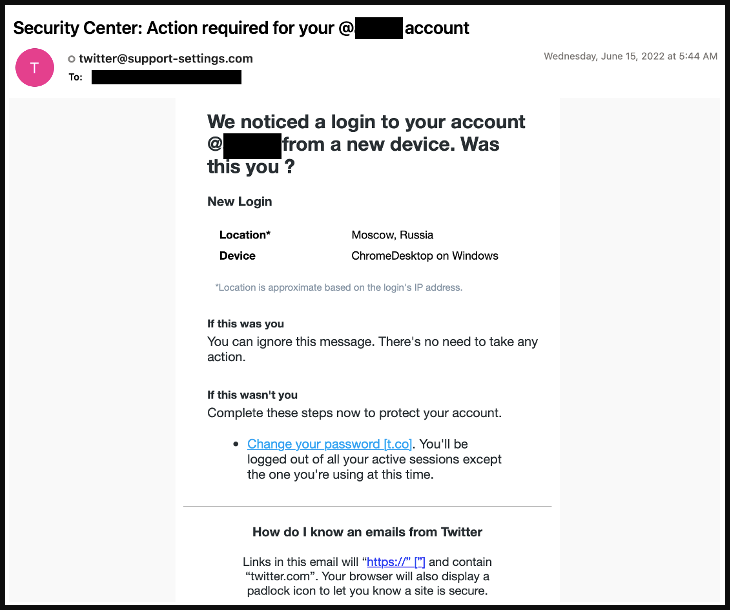
Lastly, Turkish menace actors tracked as TA482 orchestrated credential harvesting campaigns that tried to steal journalists’ social media accounts.
Impersonating journalists
Nevertheless, not all hackers care to place within the effort to compromise journalist accounts. As a substitute, some minimize corners and go straight to assuming reporter personas to achieve out to their targets straight.
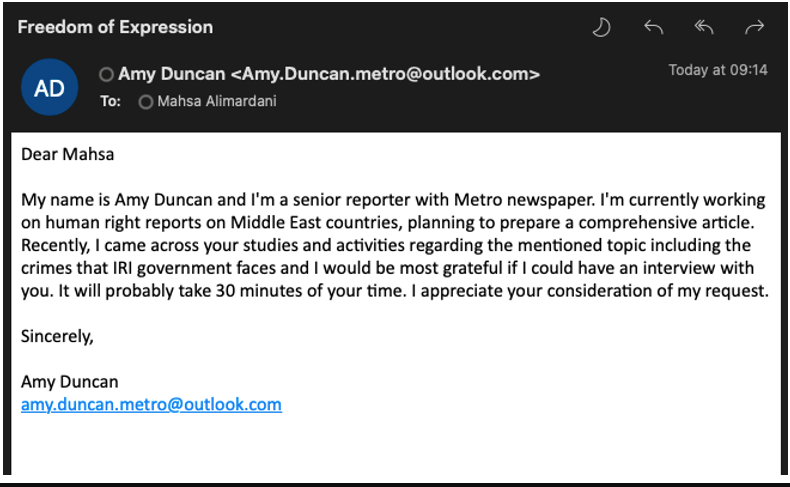
Proofpoint has seen this tactic primarily from Iranian actors like TA453 (a.ok.a. Charming Kitten), who despatched emails to lecturers and Center East coverage consultants posing as reporters.
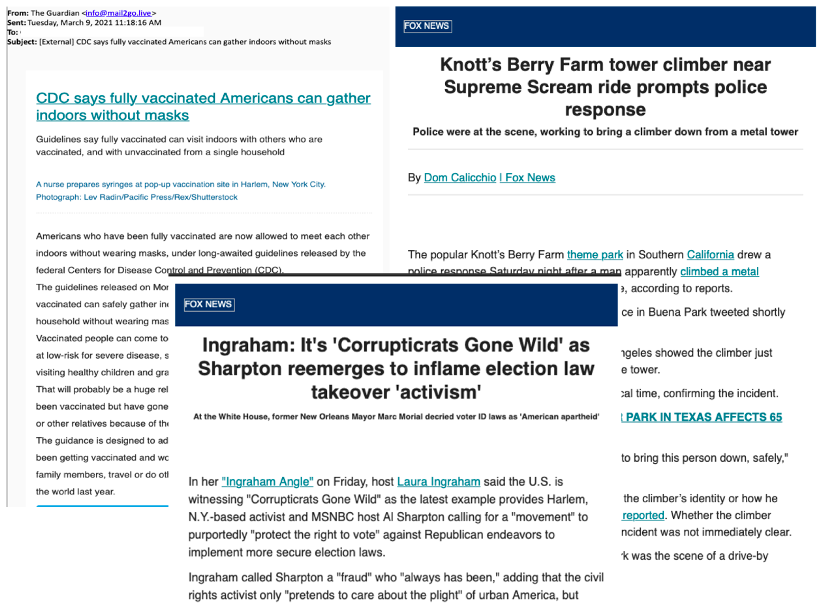
One other instance is TA456 (aka Tortoiseshell), that additionally masquerades its emails as newsletters from the Guardian or Fox information, hoping for profitable malware supply to the goal.
Lastly, Proofpoint highlights the exercise of Iranian hackers TA457, who, between September 2021 and March 2022, launched media-targeting campaigns each two to a few weeks.
APTs are anticipated to proceed focusing on journalists utilizing phishing methods, malware droppers, and varied social engineering techniques.
Sadly, media organizations and their workers are open to the general public and will turn into victims of social engineering that might result in compromising their entry to delicate data.
[ad_2]
Source link


