[ad_1]

The North Korean APT group ‘Lazarus’ (APT38) is exploiting VMWare Horizon servers to entry the company networks of power suppliers in america, Canada, and Japan.
Lazarus is a state-backed risk actor recognized for conducting espionage, knowledge theft, and cryptocurrency stealing campaigns over the previous decade. The risk actors are answerable for lots of of refined assaults internationally.
In line with researchers at Cisco Talos, who uncovered the newest operation, Lazarus focused the power organizations between February and July 2022, leveraging public VMWare Horizon exploits for preliminary entry.
From there, they used customized malware households like ‘VSingle’ and ‘YamaBot’ and a beforehand unknown distant entry trojan (RAT) named ‘MagicRAT’ that’s used to seek for and steal knowledge from contaminated gadgets.
Symantec’s risk hunters analyzed the identical marketing campaign in April and ASEC researchers in Might. Nonetheless, Cisco’s report goes deeper to unveil many extra particulars in regards to the risk actor’s exercise.
A number of assault methods
Cisco Talos presents a number of assault methods that illustrate Lazarus’ newest strategies, techniques, and procedures (TTPs) and spotlight the flexibility of the delicate hacking group.
Within the first case, the risk actors exploit VMWare servers susceptible to Log4Shell flaws to run shellcode that establishes a reverse shell for operating arbitrary instructions on the compromised endpoint.
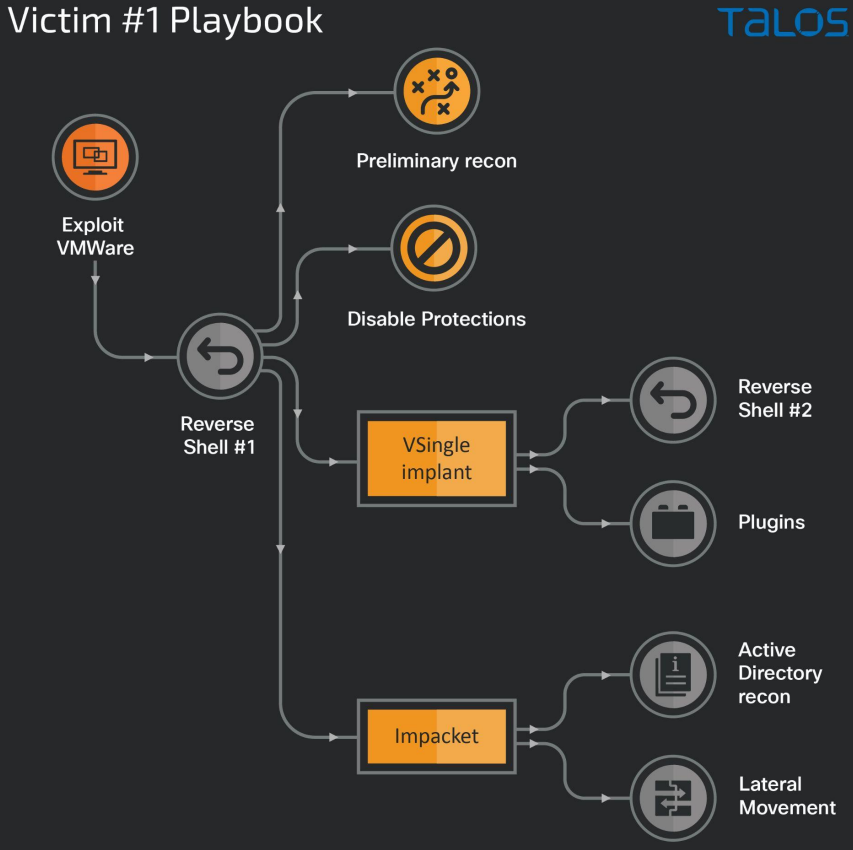
Since VMWare Horizon runs with excessive privileges, Lazarus can deactivate Home windows Defender by way of registry key modifications, WMIC, and PowerShell instructions earlier than deploying VSingle.
The VSingle backdoor helps superior community reconnaissance instructions, prepares the bottom for stealing credentials, creates new admin customers on the host, and at last establishes a reverse shell reference to the C2 to fetch plugins that enrich its performance.
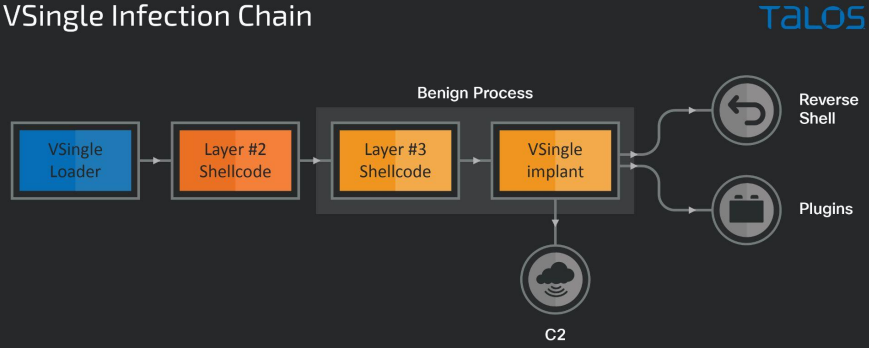
Within the second case offered within the report, which issues a unique sufferer, the preliminary entry and reconnaissance observe related patterns, however this time, the hackers dropped MagicRAT together with VSingle.
Talos revealed a separate publish on MagicRAT yesterday, detailing all of the capabilities of this beforehand unseen trojan.
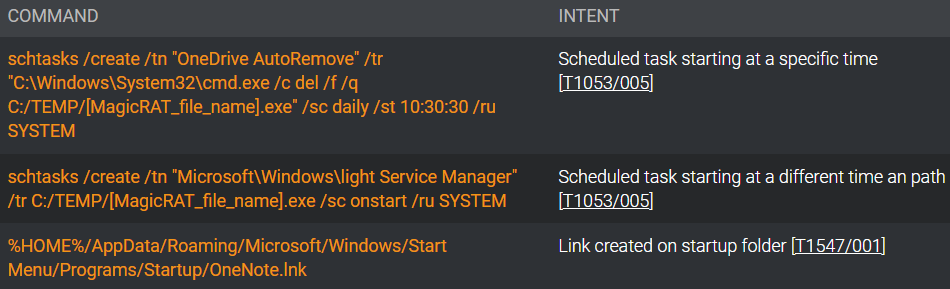
MagicRAT can set up persistence by itself by executing hardcoded instructions that create the required scheduled duties, assist in system reconnaissance, and fetch extra malware from C2, just like the TigerRAT.
Within the third intrusion case, Lazarus deploys YamaBot, a customized malware written in Go, that includes customary RAT capabilities similar to:
- Record information and directories.
- Ship course of info to C2.
- Obtain information from distant areas.
- Execute arbitrary instructions on the endpoints.
- Uninstall itself
The Japanese CERT linked YamaBot with Lazarus in July 2022, highlighting its encrypted C2 communication capabilities.
Lazarus assault chain diversification isn’t restricted to the ultimate malware payloads however extends to the proxy or reverse tunneling instruments and credential harvesting strategies.
In some instances, the hackers employed the Mimikatz and Procdump instruments, whereas in others, they exfiltrated copies of registry hives containing AD credentials.
“In a single occasion, the attackers tried to acquire Lively Listing info on one endpoint by way of PowerShell cmdlets. Nonetheless, a day later, the attackers used adfind.exe to extract related info on the identical endpoint,” explains Cisco Talos within the report.
The thought behind these variations is to combine up TTPs and make attribution, detection, and protection more difficult for incident responders.
As highlighted on this report, Lazarus is intently monitored by cybersecurity corporations, to allow them to’t afford to develop into lazy in diversifying their assault chains.
This diversification in assaults is illustrated within the Lazarus hacker’s big selection of assaults, together with their concentrating on of IT job seekers, the creation of pretend cryptocurrency buying and selling apps, the creation of trojanized growth instruments, using ransomware as decoys, and the huge $620 million theft of cryptocurrency theft from the Ronin bridge.
[ad_2]
Source link


