[ad_1]
182 complete views, 182 views immediately
In response to Kaspersky’s Digital Footprint Intelligence (DFI) report for APAC, database leaks within the area account for 95% of the full quantity of commercials. Singapore’s and Australia’s information leaks market are by far the biggest when wanting on the weighted GDP quantities of orders.
The report highlights outcomes collected final 12 months for organizations and even nations to control potential exterior threats and keep knowledgeable about potential cybercriminal actions, together with ones being mentioned on the Darknet.
Monitoring of exterior information sources in Kaspersky’s Digital Footprint Intelligence service, together with Darknet sources, supplies insights into cybercriminal exercise via totally different levels of assault lifecycle. Within the second a part of the report, the corporate presents Darknet evaluation outcomes.

There are two main kinds of information discovered when analyzing a corporation’s digital footprint: fraudulent actions and cyberattack footprints. Whereas Kaspersky found quite a few fraud indicators, the main focus within the report stays on assault detection.
Darknet exercise associated to assault influence (commercials on promoting information leaks and compromised information) dominates the statistics as these are unfold over time, the place criminals promote, resell and repack plenty of information leaks from the previous.
Stage 1: Curiosity to purchase entry
Cybercriminals who’re in search of preliminary entry affords know that there’s a giant market of such commercials. Organizations from Australia, India, mainland China, and Pakistan are the most important adversaries’ curiosity to begin an assault. These nations had been current in 84% of advertisements from the assault preparation class.
Pakistan and Australia appeal to enormous curiosity as seen by the variety of orders weighted with their GDP.

Wanting on the measurement of infrastructure, companies, and industrialization – mainland China poses comparatively low curiosity for adversaries. This may increasingly point out the presence of a language barrier cybercriminal scene within the APAC area or the problems with network-level entry to organizations within the nation.
Entry purchase order is a request to purchase entry to a single or an inventory of particular organizations or industries in a selected area.
Insider exercise purchase orders, nevertheless, are requests to purchase insider providers which may result in credentials or information leaks, supply of data gathering service (e.g., PII information exfiltration by request). These orders are essentially the most inconclusive kind of findings for remediation planning.
Stage 2: Orders for entry – able to execute
Essentially the most promising findings are from the assault execution stage: artifacts are stating that adversaries have capabilities or have already got entry to organizations’ networks or providers, however there isn’t a enterprise influence but. When it comes to commercials on the Darknet, indicating an assault executed, Australia, India, mainland China and the Philippines cowl 75% of these detected by Kaspersky.
It’s divided into three sorts:
-
Preliminary entry brokers – Promote orders for particular organizations, or bulk orders with organizations grouped by business and/or area.
-
Insider exercise promote orders – Request to promote insider providers that may result in credentials leak, supply of data gathering service (e.g. PII information exfiltration by request), or information leak. The supply is often an insider’s dealer.
-
Malware logs – Credential stealing malware (stealers) acquire credentials into resalable or in any other case accessible information with account usernames and passwords.
The Philippines, Pakistan, Singapore, Australia, and Thailand organizations are most attacked when weighted with GDP.
The Philippines, India, and mainland China are dominating the insider providers market with 82% of orders turnover.
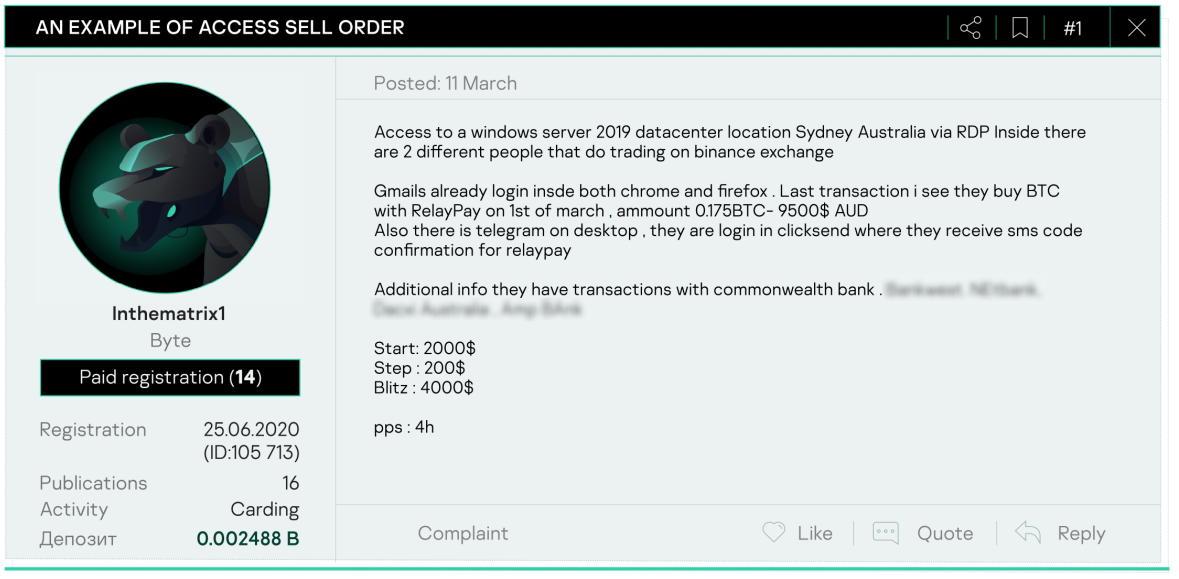
Stage 3: Information leaks and information on the market
As soon as a knowledge leak happens, the sale or free entry to the stolen info will comply with. An indicator of compromise may be information leaks in addition to insider exercise orders – sale or free entry to inside information, together with however shouldn’t be restricted to databases, confidential paperwork, PII, bank cards, VIP info, monetary information and plenty of extra.
Organizations from Australia, mainland China, India, and Singapore take 84% of all information leaks promote orders positioned on the Darknet.
Singapore’s and Australia’s information leaks market are by far the biggest when wanting on the weighted with GDP quantities of orders.
It needs to be famous that the Philippines, Pakistan, and Thailand organizations had been among the many adversaries curiosity to start an assault or appeared as already compromised, however the quantity of knowledge leaks is on par with different nations from the center of the group.
“Cybercriminal operations beneath the floor net are clearly busy. From assault preparation and execution, to the influence of a knowledge leak after which promoting and reselling of stolen info, this functioning malicious system is a severe menace for companies and organizations right here in APAC,” says Chris Connell, Managing Director for Asia Pacific at Kaspersky.
“Promoting information and entry to the businesses usually goes hand in hand. This implies a profitable assault to your group may be two pronged. Your confidential info may be stolen and be bought, and these cybercriminals can open and provide your contaminated system to extra malicious teams. A double whammy that requires a proactive protection that features sturdy incident response and Darknet monitoring capabilities via real-time and in-depth menace intelligence stories,” he provides.
Learn how to shield your organization from these type of threats
Demand for company and private information on the black market is excessive, and it doesn’t at all times contain focused assaults. Attackers might acquire entry to the infrastructure of a random firm to promote it to blackmailers or different superior cybercriminals later.
An assault like this will have an effect on an organization of any measurement, massive or small, as a result of company system entry is commonly priced reasonably on underground boards, particularly in comparison with the potential harm to a enterprise.
Sellers on the darkish net most frequently provide distant entry by way of RDP. To guard company infrastructure from assaults via distant entry and management providers, ensure the connection by way of this protocol is safe by:
*The report used GPD from https://information.worldbank.org/
Associated
[ad_2]
Source link


