[ad_1]

The North Korean espionage-focused actor often called Kimsuky has been noticed utilizing three totally different Android malware strains to focus on customers positioned in its southern counterpart.
That is in response to findings from South Korean cybersecurity firm S2W, which named the malware households FastFire, FastViewer, and FastSpy.
“The FastFire malware is disguised as a Google safety plugin, and the FastViewer malware disguises itself as ‘Hancom Workplace Viewer,’ [while] FastSpy is a distant entry software primarily based on AndroSpy,” researchers Lee Sebin and Shin Yeongjae mentioned.
Kimsuky, additionally recognized by the names Black Banshee, Thallium, and Velvet Chollima, is believed to be tasked by the North Korean regime with a world intelligence-gathering mission, disproportionately focusing on people and organizations in South Korea, Japan, and the U.S.
This previous August, Kaspersky unearthed a beforehand undocumented an infection chain dubbed GoldDragon to deploy a Home windows backdoor able to stealing info from the sufferer corresponding to file lists, consumer keystrokes, and saved net browser login credentials.
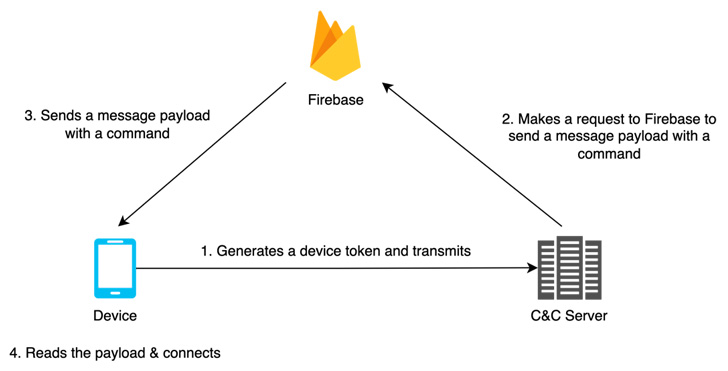
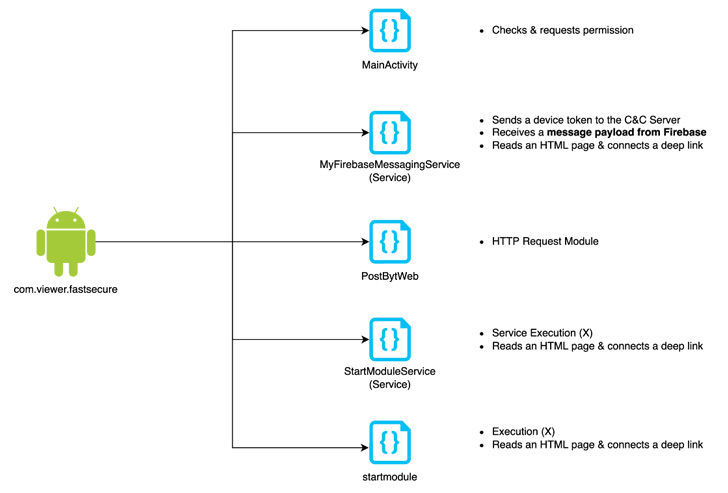
The superior persistent risk can also be recognized to an Android model of AppleSeed implant to execute arbitrary actions and exfiltrate info from the contaminated units.
FastFire, FastViewer, and FastSpy are the newest additions to its evolving Android malware arsenal, that are designed to obtain instructions from Firebase and obtain further payloads.
“FastViewer is a repackaged APK by including arbitrary malicious code inserted by an attacker to the traditional Hancom Workplace Viewer app,” the researchers mentioned, including the malware additionally downloads FastSpy as a next-stage.
The rogue apps in query are under –
- com.viewer.fastsecure (Google 보안 Plugin)
- com.tf.thinkdroid.secviewer (FastViewer)
Each FastViewer and FastSpy abuse Android’s accessibility API permissions to satisfy its spying behaviors, with the latter automating consumer clicks to grant itself in depth permissions in a way analogous to MaliBot.

FastSpy, as soon as launched, permits the adversary to grab management of the focused units, intercept cellphone calls and SMSes, observe customers’ places, harvest paperwork, seize keystrokes, and file info from the cellphone’s digital camera, microphone, and speaker.
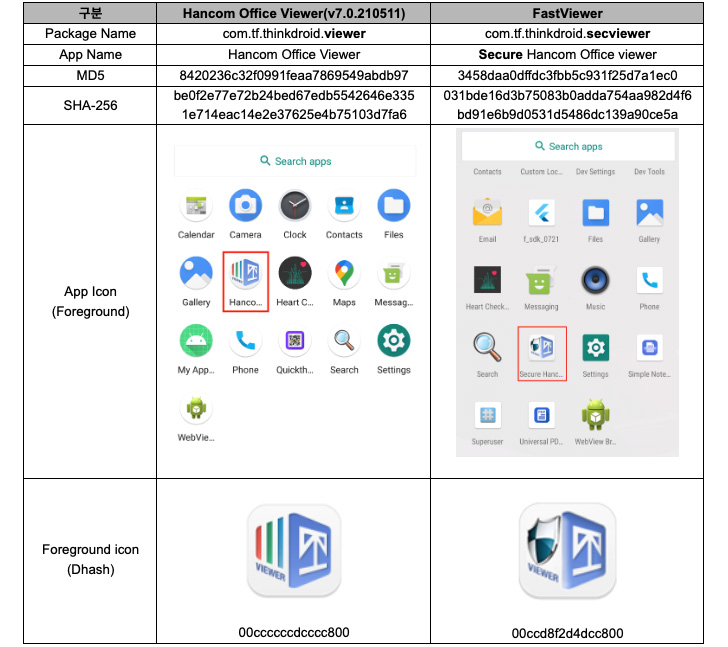
S2W’s attribution of the malware to Kimsuky relies on overlaps with a server area named “mc.pzs[.]kr,” which was beforehand employed in a Could 2022 marketing campaign recognized as orchestrated by the group to distribute malware disguised as North Korea associated press releases.
“Kimsuky group has repeatedly carried out assaults to steal the goal’s info focusing on cellular units,” the researchers mentioned. “As well as, numerous makes an attempt are being made to bypass detection by customizing Androspy, an open supply RAT.”
“Since Kimsuky group’s cellular focusing on technique is getting extra superior, it’s essential to watch out about subtle assaults focusing on Android units.”
[ad_2]
Source link


