[ad_1]
677 complete views, 3 views immediately
Phishing is a time period usually heard within the information. It’s cybercriminals’ go-to infiltration approach, as a result of it’s easy, and since it really works.
Mainly, phishing is a kind of Web fraud that seeks to amass a consumer’s credentials by deception. It contains theft of passwords, bank card numbers, checking account particulars and different confidential info.
“Cybercriminals observe tendencies. They know the most recent matters they’ll successfully piggyback on. It’s a social engineering approach that performs on our human minds, that’s why it’s troublesome to withstand clicking an unknown hyperlink, which can ultimately change into malicious,” says Adrian Hia, Managing Director for Asia Pacific at Kaspersky.
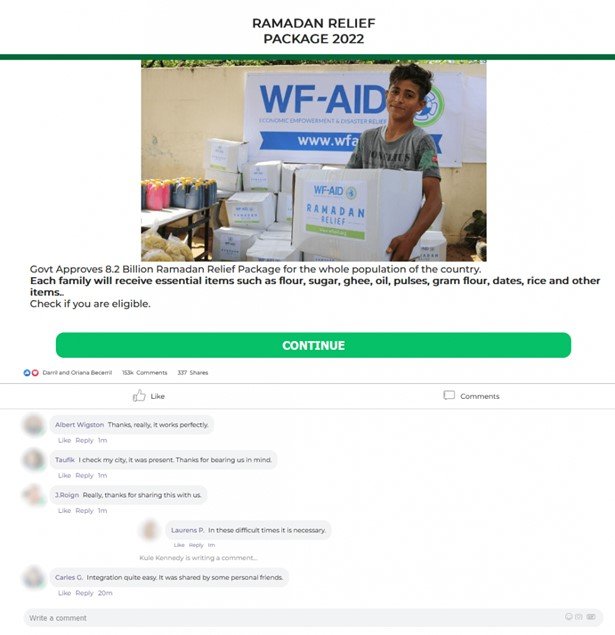
For example, in 2022, key phishing matters monitored by Kaspersky specialists associated to compensations, bonuses, and even refunds.
Bonuses and compensation are arduous to disclaim in instances of disaster and instability, which is why “monetary help” is steadily promised by con artists to swindle customers out of their cash.
“Promotional campaigns by main banks” have been a preferred bait in 2022. Guests to a fraudulent internet web page have been provided to obtain a one-time fee or to take a service high quality survey for a price.
In Muslim international locations, scammers promised to ship charity packages, purportedly below a “Ramadan Reduction” program that geared toward serving to low-income households through the Ramadan quick. The fasting interval usually sees greater costs for meals and family merchandise, whereas observers purchase greater than they usually do and could also be confronted with a scarcity of cash.
Rising utility charges and a rise within the worth of pure assets have prompted a number of governments to start out discussing compensations for the inhabitants. Payout notices may arrive by mail, e mail, or as a textual content message.
Cybercriminals tried to make the most of the scenario by creating internet pages that mimicked authorities web sites, promising money for overlaying utility funds or compensation of utility bills. Guests have been sometimes requested to offer private particulars below the pretext of checking that they have been eligible, or just to fill out a questionnaire.
In Singapore, scammers provided a refund of water provide prices, purportedly due to double billing. An vitality or useful resource disaster was not used as a pretext on this explicit case, however refunds have been nonetheless provided within the identify of the water provide authority.
“Our options blocked greater than 43 million phishing assaults towards our customers in Southeast Asia final 12 months. Clearly, phishing is a software used steadily by cybercriminals. As a result of its nature requires a consumer’s participation – the mere clicking a hyperlink or opening of a file – it’s pressing for everybody to understand how phishing actually works so we are able to keep away from falling prey towards it,” provides Hia.
How a phishing marketing campaign unfolds
In 2022, Kaspersky specialists noticed a rise in spear (or focused) phishing assaults concentrating on companies world wide. Along with typical campaigns consisting of 1 stage, there have been assaults in a number of levels. Within the first e mail, scammers within the identify of a possible consumer requested the sufferer to specify details about its services and products. After the sufferer responds to this e mail, the attackers begin a phishing assault.
Stage 1: Attackers ship an e mail within the identify of an actual commerce group requesting extra details about the sufferer firm’s merchandise. The e-mail textual content appears to be like believable and has no suspicious components, resembling phishing hyperlinks or attachments. A sender’s e mail deal with from a free area, like gmail.com, might elevate doubts. The e-mail on the screenshot under is shipped from an deal with on this area, and the corporate identify within the From subject is completely different to its identify within the signature.
It’s value noting that using free domains shouldn’t be typical for spear phishing within the identify of organizations, as a result of such domains are hardly ever utilized in enterprise.
Most frequently in focused assaults, attackers both use spoofing of the authentic area of the group they’re pretending to be, or register domains just like the unique one. As well as, Google and Microsoft are fairly fast in blocking e mail addresses noticed sending spam. That is the almost definitely cause why attackers used completely different addresses within the From header (the place the e-mail got here from) and Reply-to header (the place the reply will go when clicking “Reply” in your e mail consumer).
This implies the sufferer responds to a different deal with, which can be positioned in one other free area, resembling outlook.com. The deal with within the Reply-to header shouldn’t be used for spam, and correspondence with it’s initiated by the sufferer, so it’s much less prone to be blocked rapidly.
Stage 2: After victims reply to a primary e mail, attackers ship a brand new message, asking them to go to a file-sharing web site and think about a PDF file with a accomplished order, which could be discovered by way of the hyperlink.
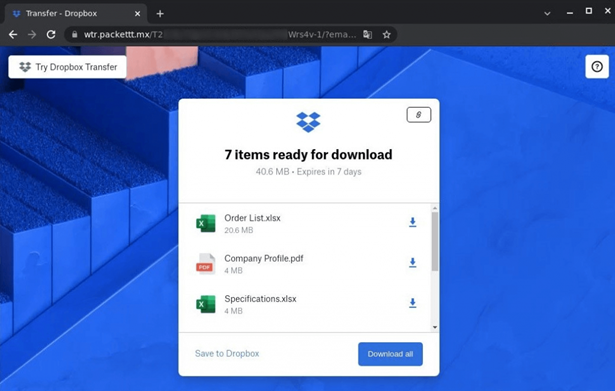
Stage 3: By clicking the hyperlink, the consumer is taken to a faux web site generated by a well known phishing package. It’s a pretty easy software that generates phishing pages to steal credentials from particular assets. Our options blocked faux WeTransfer and Dropbox pages created with this package.
Within the phishing marketing campaign described above, the phishing web site mimics a Dropbox web page with static file photos and a obtain button. After clicking any aspect of the interface, the consumer is taken to a faux Dropbox login web page that requests legitimate company credentials.
Stage 4: When victims try to log in, their usernames and passwords are despatched to https://
The marketing campaign started in April 2022, with malicious exercise peaking in Might, and ended by June.
Kaspersky recognized targets for this marketing campaign world wide, together with the next international locations: Russia, Bosnia and Herzegovina, Singapore, USA, Germany, Egypt, Thailand, Turkey, Serbia, Netherlands, Jordan, Iran, Kazakhstan, Portugal, and Malaysia.

Phishing tendencies in 2023
Instances of disaster create the preconditions for crime to flourish, together with on-line. Kaspersky specialists predict scams promising compensation and payouts from authorities companies, massive firms and banks are prone to stay in style amongst cybercriminals subsequent 12 months.
The unpredictability of the foreign money market and departure of particular person corporations from particular international locations’ markets will seemingly have an effect on the variety of scams related to on-line buying. On the identical time, the COVID-19 subject, in style with cybercriminals in 2020 and 2021, however already starting to wane in 2022, will lastly stop to be related and will probably be changed by extra urgent world points.
As well as, Kaspersky additionally has seen a rise in focused phishing assaults the place scammers don’t instantly transfer on to the phishing assault itself, however solely after a number of introductory emails the place there may be energetic correspondence with the sufferer. This development is prone to proceed. New tips are additionally prone to emerge within the company sector in 2023, with assaults producing vital earnings for attackers.
Associated
Unfold the love
1 1
Share
[ad_2]
Source link


