[ad_1]
Getting root entry inside certainly one of Starlink’s dishes requires a number of issues which can be onerous to return by: a deep understanding of board circuitry, eMMC dumping {hardware} and expertise, bootloader software program understanding, and a {custom} PCB board. However researchers have confirmed it may be finished.
Of their speak “Glitched on Earth by People: A Black-Field Safety Analysis of the SpaceX Starlink Person Terminal,” researchers at KU Leuven in Belgium detailed at Black Hat 2022 earlier this 12 months how they had been in a position to execute arbitrary code on a Starlink Person Terminal (i.e., a dish board) utilizing a custom-built modchip by means of a voltage fault injection. The speak befell in August, however the researchers’ slides and repository have lately made the rounds.
There is not any quick menace, and the vulnerability is each disclosed and restricted. Whereas bypassing signature verification allowed the researchers to “additional discover the Starlink Person Terminal and networking facet of the system,” slides from the Black Hat speak notice that Starlink is “a well-designed product (from a safety standpoint).” Getting a root shell was difficult, and doing so did not open up apparent lateral motion or escalation. However updating firmware and repurposing Starlink dishes for different functions? Maybe.
Nonetheless, satellite tv for pc safety is much from merely theoretical. Satellite tv for pc supplier Viasat noticed 1000’s of modems knocked offline by AcidRain malware, pushed by what most assess to be Russian state actors. And whereas the KU Leuven researchers notice how unwieldy and tough it could be to connect their {custom} modchip to a Starlink terminal within the wild, many Starlink terminals are positioned in essentially the most distant areas. That provides you a bit extra time to disassemble a unit and make the greater than 20 fine-point soldering connections detailed in slide photographs.
-
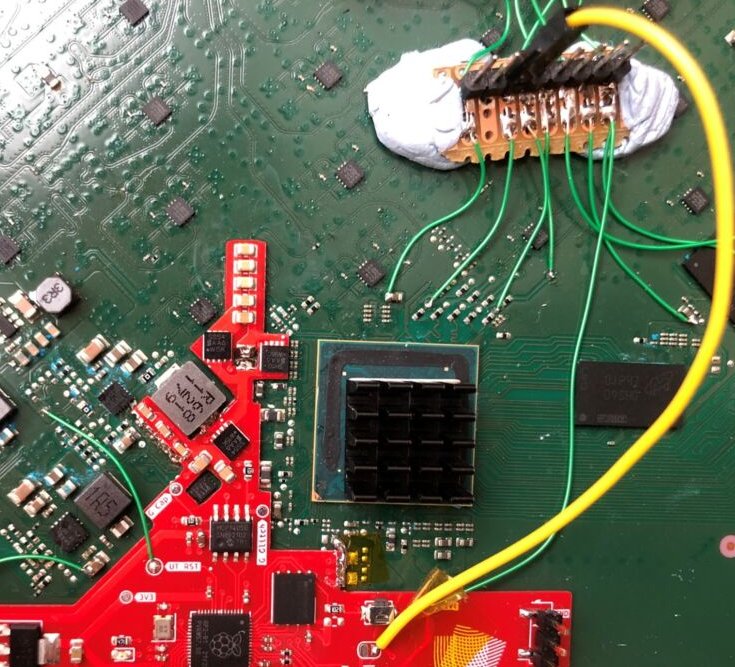
Studying from eMMC take a look at factors to extract and patch Starlink’s firmware.
-
The essential design of the Starlink intruder modchip, with a Pi-designed processor at its core
-
No person stated getting root entry to house was going to be straightforward.
-
How you can take a look at your satellite tv for pc safety proof-of-concept while you work inside a college.
It isn’t straightforward to summarize the quite a few strategies and disciplines used within the researchers’ {hardware} hack, however right here is an try. After some high-level board evaluation, the researchers positioned take a look at factors for studying the board’s eMMC storage. Dumping the firmware for evaluation, they discovered a spot the place introducing errant voltage into the core system on a chip (SoC) may modify an necessary variable throughout bootup: “growth login enabled: sure.” It is sluggish, it solely works often, and the voltage tampering could cause a number of different errors, nevertheless it labored.
The modchip utilized by the researchers is centered round a RaspberryPi RP2040 microcontroller. Not like most Raspberry Pi {hardware}, you may nonetheless seemingly order and obtain the core Pi chip, do you have to embark on such a journey. You may learn extra concerning the firmware dumping course of within the researchers’ weblog publish.
[ad_2]
Source link


